Introduction
A VPN (Virtual Private Network) is the connection between two devices using IPsec to protect data.
IPsec is a protocol suite for securing IP networks by authenticating and encrypting IP packets. IPsec protects one or more paths between a pair of hosts, a pair of security gateways, or a security gateway and a host.
What does IPsec do?
IPsec provides the following security services for traffic at network Layer 3 (IP):
-
Data origin authentication—Identifying who sent the data.
-
Confidentiality (encryption)—Ensuring that the data has not been read en route.
-
Connectionless integrity (authentication)—Ensuring the data has not been changed en route.
-
Replay protection—Detecting packets received more than once to help protect against denial of service attacks.
The operation of IPsec is based upon negotiated connections between peer devices. These connections are called Security Associations.
Starting the Wizard
When the Router is turned on for the first time, you can connect a network cable to port 1, this will make the Router configure the IP 192.168.1.1/24 in Vlan 1, allowing access to the Graphical Interface of the unit. The Wizard uses Vlan 1 as part of the configuration, if you dont want to use the default IP address but still want to configure the VPN using the Wizard, assign the IP address of your choice to Vlan 1.
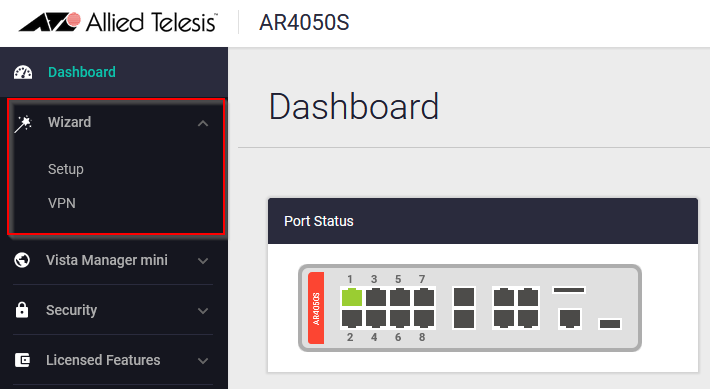
Log into the Router using the GUI and select the Wizard option from the left side menu.
 g
g
You need to configure the IP address that the Router will use to connect to the Internet in one of the ETHs port.
Select Setup >> Start Wizard >> Select Item; a drop down menu will appear, then select the proper method that the Router will use to get IP address, for this example "Fixed" is selected.
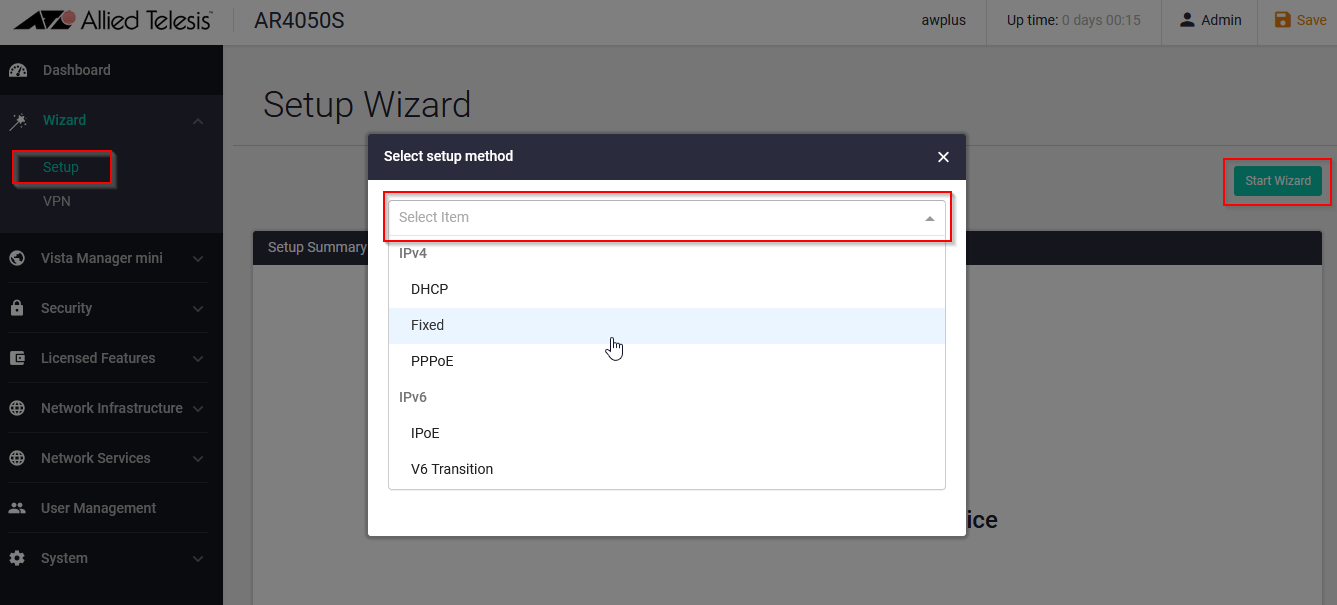
Fill in the required information and select the interface (ETH1) you want to use.
When the confirmation screen appears select "Apply".
Now the Router has an IP address that it uses to communicate over the Internet.
To Configure the VPN, select VPN >> Start Wizard, fill in the required information and select Next.
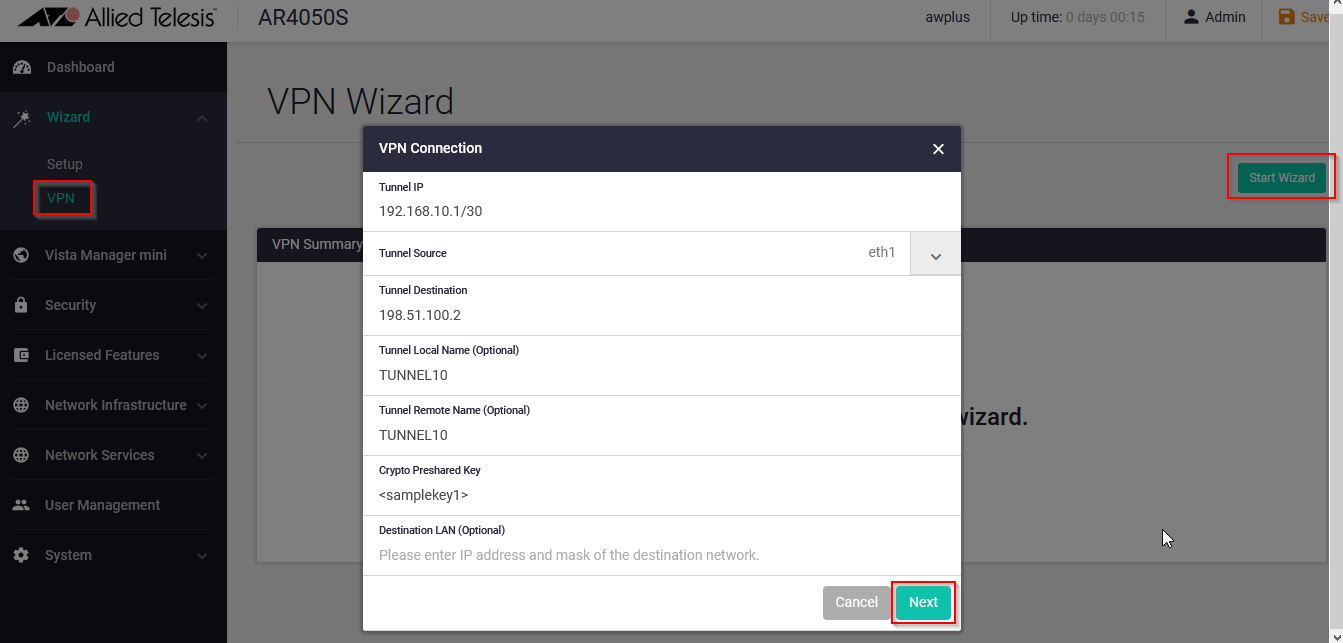
Tunnel IP: Specify an IPv4 source address for packets being encapsulated in the IPsec tunnel.
Tunnel Source: Specify the interface name for packets being encapsulated in the IPsec tunnel.
Tunnel Destination: Specify a destination IPv4 address for the remote end of the tunnel (This should be the public IP that the other side of the VPN is using to reach out the Internet).
Tunnel Local Name: Specify an IPSec tunnel hostname to send to the peer for authentication when you apply tunnel protection IPsec to encrypt the packets and configure an ISAKMP key.
Tunnel Remote Name: Specify a tunnel remote name to authenticate the tunnel’s remote peer device when you apply tunnel protection IPsec to encrypt the packets and configure an ISAKMP key.
Crypto Preshared Key: Configure an ISAKMP authentication key.
When the confirmation screen appears select "Apply".
The Wizard will create the necessary firewall rules in order to stablish the VPN.
Remember to save the configuration by clicking the "Save" button in the upper right corner.
Configuration example in Command Line
Here is an example of the configuration that is created by the Wizard.
Router public IP address
interface eth1
ip address 192.0.2.2/30
Firewall Zones and Entities
zone private
network lan
ip subnet 0.0.0.0/0 interface vlan1
ip subnet 192.168.10.0/30
zone public
network wan
ip subnet 0.0.0.0/0 interface eth1
host eth1
ip address 192.0.2.2
Firewall and NAT rules
firewall
rule 10 permit isakmp from public.wan.eth1 to public.wan
rule 20 permit isakmp from public.wan to public.wan.eth1
rule 30 permit esp from public.wan.eth1 to public.wan
rule 40 permit esp from public.wan to public.wan.eth1
rule 50 permit any from private to private
rule 60 permit any from private to public
rule 70 permit dns from public.wan.eth1 to public.wan
protect
nat
rule 10 masq any from private to public
enable
Applications needed for the VPN
application esp
protocol 50
application isakmp
protocol udp
sport 500
dport 500
Tunnel configuration
interface tunnel1
tunnel source eth1
tunnel destination 198.51.100.2
tunnel local name TUNNEL10
tunnel remote name TUNNEL10
tunnel protection ipsec
tunnel mode ipsec ipv4
ip address 192.168.10.1/30
Default Gateway
ip route 0.0.0.0/0 192.0.2.1
Some Show commands
show ipsec peer
Use this command to show IPSec information on a per peer basis.
awplus#show ipsec peer 198.51.100.2
IPsec
Selectors (local:remote)
Address: 0.0.0.0/0 : 0.0.0.0/0
Protocol: any:any
Port: any:any
Mark: 16395:16395
Profile: default
SPI (In:Out): c5b7af17:ce882b06
Selectors: 0.0.0.0/0 0.0.0.0/0
Proto: ESP
Mode: tunnel
Encryption: AES256
Integrity: SHA256
Expires: 28606s
ISAKMP
LocalID: TUNNEL10
RemoteID: TUNNEL10
Cookies (Initiator:Responder) 2e85e974129e5a50:34765833120d46d4
Ver: 2 Lifetime: 82495s State: Established
Authentication: PSK Group: 14
Encryption: AES256 NATT: no
Integrity: SHA256 DPD: yes
show ipsec sa
Use the command show ipsec sa to show the state of the IPsec security association formed between two IPsec peers.
awplus##show ipsec sa
-----------------------------------------------------------------------------
Peer SPI (in:out) Mode Proto Expires
Encryption Integrity PFS
-----------------------------------------------------------------------------
TUNNEL10 c5b7af17:ce882b06 tunnel ESP 28659s
(198.51.100.2) AES256 SHA256 -
show ipsec policy
Use the command show IPSec policies.
awplus#show ipsec policy
IPsec policy information
--------------------------------------
Name: tunnel10
Local Address: 192.0.2.2 (TUNNEL10)
Remote Address: 198.51.100.2 (TUNNEL10)
Selectors (local:remote)
Address: 0.0.0.0/0 : 0.0.0.0/0
Protocol: any:any
Port: any:any
Mark: 16395:16395
Mode: tunnel
Profile: default
show isakmp key
Use the command show isakmp key to show the ISAKMP pre-shared key.
awplus#show isakmp key
Hostname/Address/Policy PSK EAP
--------------------------------------------------------------------------
TUNNEL10 <samplekey1> -
For more information about IPSec and VPN, refer to the Internet Protocol Security (IPsec) Feature Overview and Configuration Guide