Introduction
This article describes some common attacks which can be executed with unauthorized access to switch network, the risk of these attacks, and how to counter them using features implemented in Allied Ware Plus.
Sample Attacks
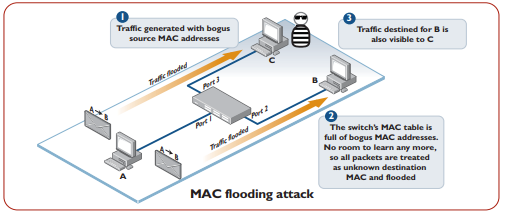
MAC Flooding
When executing a MAC flooding attack, the attacker would use a device attached to a switch, then flood the port with random generated MAC address. With no protection configured, the switch will keep learning the random MAC address until its CAM (Content-Addressable Memory) table is filled. after the CAM table is filled, the switch is no longer able to learn new MAC address, it will have to forward any incoming traffic to all ports with the risk that the traffic can be sniffed for valuable information such as unencrypted credentials.
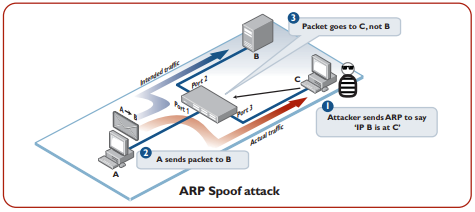
ARP spoofing
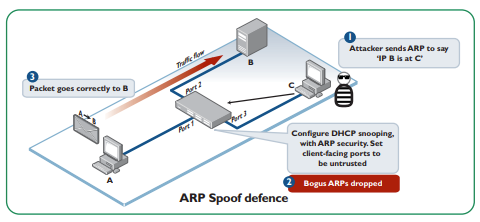
The attacker sends out forged ARP reply with false MAC address and IP address information to the switch network. When the reply is received by the hosts on the network, they update their ARP table based on the false information in the reply and start forwarding traffic meant for a legitimate user to the false MAC address(usually the attacker). the attacker can then forward the traffic to the legitimate host while keeping a copy of valuable data if received.
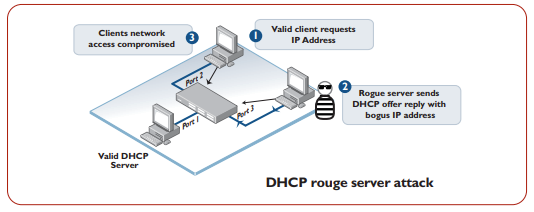
DHCP spoofing
With the DHCP spoofing attack, the attacker is connected to the switch network and listening for a DHCP Discover when a host is coming online. Once a DHCP Discover is received, the attacker quickly sends a DHCP Offer that contains an IP address, a subnet mask as well as a gateway. the host would then complete the DHCP process, start forwarding all inter-network traffic to the gateway provided by the attacker's rogue DHCP server. the attacker can then harvest information from the traffic, while forwarding them to the legit gateway to avoid detection.
Root bridge taking over
To prevent loops in the network, most of the switches run some variant of STP (spanning tree protocol). With STP there is going to be a switch in the network designated to be the root bridge, which controls the forwarding of traffic in the topology. With Root bridge take over, the attacker injects a crafted BPDU(bridge protocol data unit) with the highest priority along with a very low MAC address to gain priority over the current bridge. Without measurements to protect the STP topology, the attacker's switch can become the root bridge, This is dangerous as the attacker can now manipulate the topology and cause flooding of BPDU packets.
BPDU flooding
BPDU flooding is similar to Root bridge take over in the method of attack, however with BPDU flooding, the attacker injects a large number of crafted configuration BPDU, which are meant to be from the root bridge to provide information to the switches, these are then passed thru-out the network. When sent by the attacker in a large amount, the BPDUs quickly consume the processing power of the switches in the network and result in performance issues.
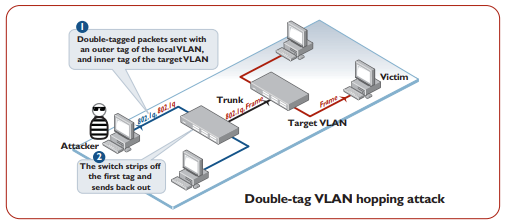
VLAN hopping
If there is a native VLAN configured on the trunk link that connects two switches, then if a double-tagged packet arrives on an access port, and its outer tag has the same VID as the native VLAN on the trunk port, then the outer VLAN will be stripped off, and the packet sent down the trunk link with its inner tag still in place. When the packet arrives at the other end of the link, the receiving switch sees it as tagged with the VID of the inner tag. The switch will then forward the packet to ports which are members of the VLAN with that VID.
Counter measure to those attacks
Place the networking equipment in securable environment
All above attack require access to the network. It would be much harder to perform if the equipment is not in an open area where anyone can walk up and plug in to one of the switch and gain access. Put switch behind locked doors, or at least in a hard to reach area greatly reduce the risk of unauthorized access.
Turn off unnecessary ports
A Port that is not being utilized can be disabled with the shut down command. this puts the port in a disabled state and preventing any access from those ports.
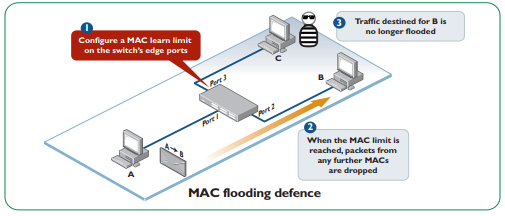
Configure port security on all ports
Port security ensure the port only allow traffic from a known MAC address or number of MAC Addresses, once the configured number is reached, an action is triggered to either drop packets with extra MAC Addresses, or disable the port. This is also a good way to counter MAC flooding attack.
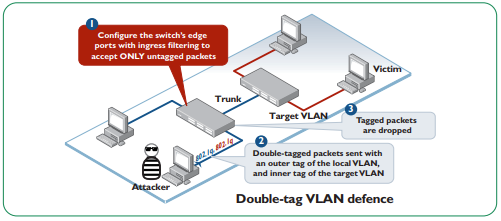
Move all ports out of default VLAN
Allied Telesis recommend utilizing dedicated VLANs for each function in network operation such as data, voice, video, security, etc. This will also counter the VLAN hopping attack. Alternatively ingress filter can be configured to drop tagged packets on an untagged port.
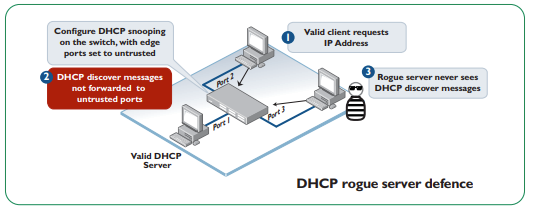
Setup DHCP snooping as well as configure ARP security
DHCP snooping can be configures so that only a trusted port can receive DHCP discovers and thus eliminate the rogue DHCP server as it will never receive DHCP discover message. This will counter DHCP spoofing attack
Once DHCP snooping is in place, ARP security can be configured as well to counter ARP spoofing
Implement Root guard and BPDU guard
Configure ports that should never be root ports to shut down if they receive low priority BPDUs:
awplus(config)# interface portx.y.z
awplus(config-if)# spanning-tree guard root
Similarly configure edge ports to shut down if they receive BPDUs:
awplus(config)# interface portx.y.z
awplus(config-if)# spanning-tree portfast bpdu-guard
Above step counters Root bridge take over as well as BPDU flooding. The network port used for attack will be shut down to prevent further attack. |