Telnet
Telnet is a network protocol that allows a user to communicate with a remote device. It is a virtual terminal protocol used mostly by network administrators to remotely access and manage devices. Administrators can access the device by telnetting to the IP address or hostname of a remote device.
One of the greatest disadvantages of this protocol is that all data, including usernames and passwords, is sent in clear text, which is a potential security risk. This is the main reason why Telnet is rarely used today and is being replaced by a much secure protocol called SSH.
SSH (Secure Shell)
SSH is a network protocol used to remotely access and manage a device. The key difference between Telnet and SSH is that SSH uses encryption, which means that all data transmitted over a network is secure from eavesdropping.
Here is an example of creating an SSH session using Putty, a free SSH client: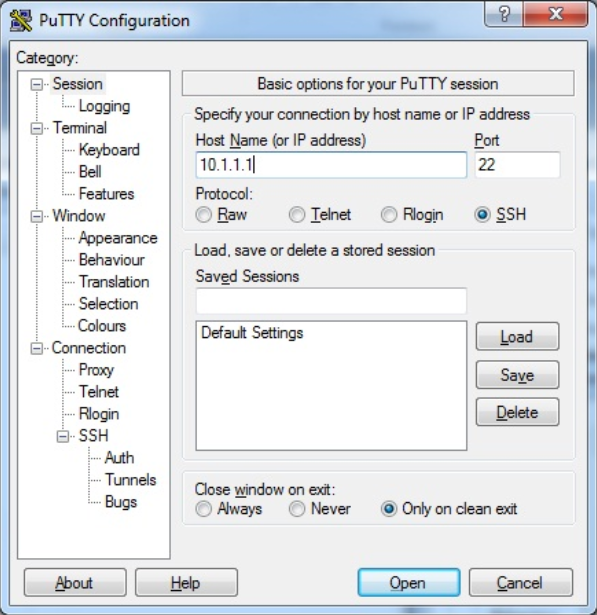 AlliedWare Plus™ uses the Secure Shell (SSH) protocol for secure remote access to the CLI. SSH encrypts the traffic involved in the CLI connection using the strong RSA encryption algorithm, thereby preventing attempts to snoop the conversation.
AlliedWare Plus™ uses the Secure Shell (SSH) protocol for secure remote access to the CLI. SSH encrypts the traffic involved in the CLI connection using the strong RSA encryption algorithm, thereby preventing attempts to snoop the conversation.
SSH servers identify themselves using a host key. Before the SSH client establishes a session with an SSH server, it confirms that the host key sent by the server matches its database entry for the server. If the database does not contain a host key for the server, then the SSH client requires you to confirm that the host key sent from the server is correct. The AlliedWare Plus device will operate as the "server" accepting incoming SSH connections.
To configure SSH under AlliedWare Plus, start by creating the RSA host key for the device:
awplus(config)# crypto key generate hostkey rsa
Then, enable the SSH process. It will automatically discover the host key that you have created and know to use that key for encrypting its sessions.
awplus(config)# service ssh
To check that the service is running, use the command:
awplus#show ssh server
Secure Shell Server Configuration
------------------------------------------------------------
SSH Server : Enabled
Protocol : IPv4,IPv6
Port : 22
Version : 2,1
Services : scp, sftp
User Authentication : publickey, password
Resolve Hosts : Disabled
Session Timeout : 0 (Off)
Login Timeout : 60 seconds
Maximum Startups : 10
Debug : NONE
Modifying SSH server parameters:
awplus(config)#ssh server v2only
awplus(config)#ssh server session-timeout 1200
awplus(config)#ssh server max-startups 5
awplus(config)#ssh server login-timeout 5
awplus#sho ssh server
Secure Shell Server Configuration
------------------------------------------------------------
SSH Server : Enabled
Protocol : IPv4,IPv6
Port : 22
Version : 2 ------------------ More secure, no real need to use v.1
Services : scp, sftp
User Authentication : publickey, password
Resolve Hosts : Disabled
Session Timeout : 1200 seconds -------- Enable automatic termination of idle Authenticated sessions
Login Timeout : 5 seconds ----------- Minimize how long an individual login attempt can tie up SSH resources
Maximum Startups : 5 ------------------- Set the number of concurrent login attempts consistent with the number of VTY sessions
Debug : NONE
When there are no registered users in the server’s database of allowed users, the SSH server does not accept SSH sessions even when enabled.
Use this command to add a username to the allow list of the SSH server.
awplus(config)# ssh server allow-users Pragya
Note: SSH server also maintains the deny list. The server checks the user in the deny list first. If a user is listed in the deny list, then the user access is denied even if the user is listed in the allow list.
Set the VTY interface to have a session timeout consistent with the SSH service, then cleared all sessions to make all configuration updates effective.
awplus(config)#line vty 0 4
awplus(config-line)#exec-timeout 20 [minutes]
% The new exec-timeout settings will apply to new sessions only
awplus(config-line)#exit
awplus(config)#exit
awplus#clear ssh all