Introducction
Port Forwarding is one of the modes of Network Address Translation (NAT) that the AR-Series firewalls support.
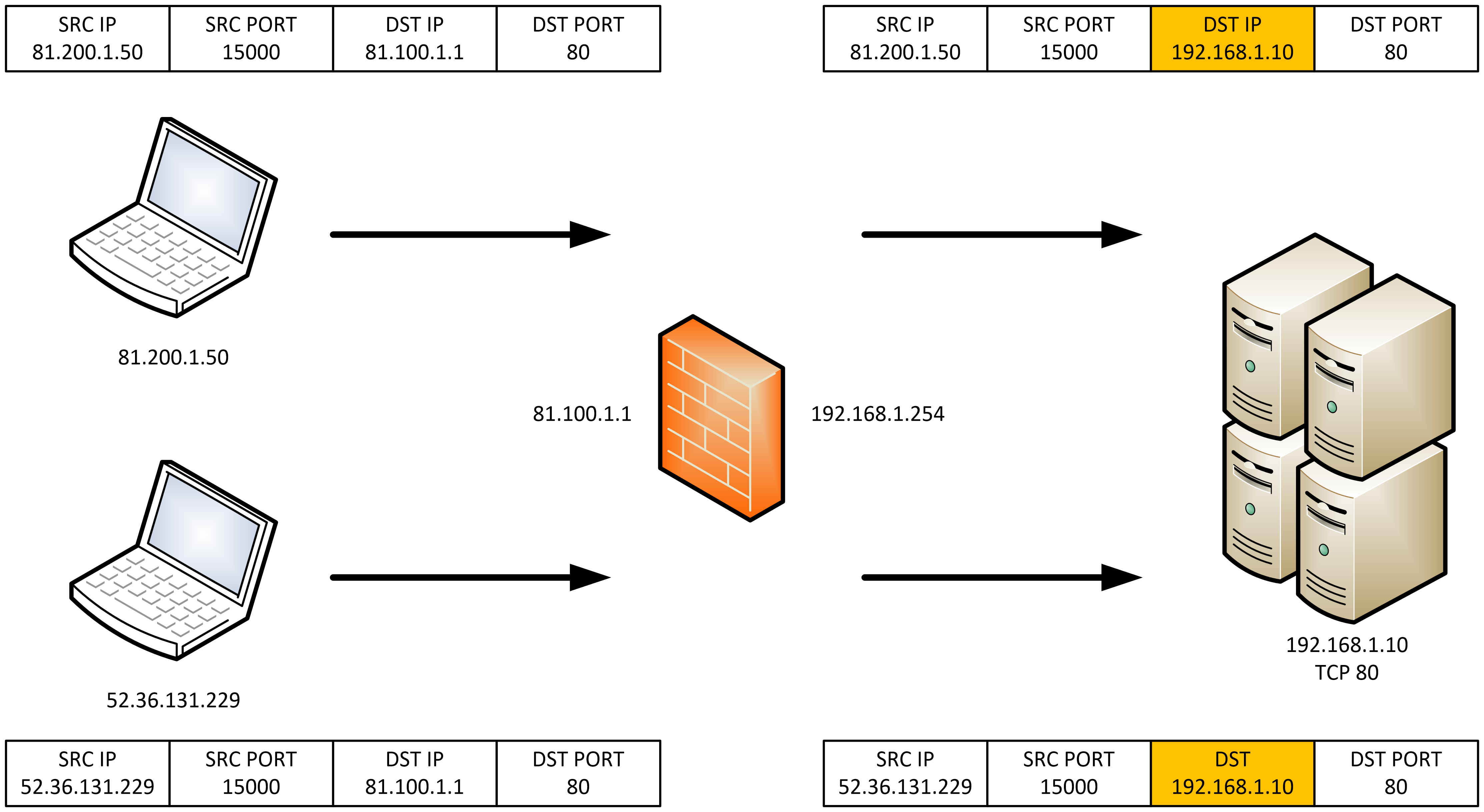
Servers on a private network are made accessible to the public network by aliasing an externally facing interface's IP to the server's IP address. The destination address of an incoming packets is translated from the external interface's IP to the private server's IP. This is an address-only translation.
By default, NAT is disabled. You can use the enable (NAT) command to explicitly enable this functionality. If firewall protection is enabled, you need to configure firewall rules that allow the application matching its source and destination entities to pass through the firewall. Portfwd rules (actions) are applied before any other firewall rules and masq rules (actions) are applied after any other firewall rules.
Configuring NAT Port forwarding
Port forwarding rules are constructed as follows:
rule [<1-65535>] portfw <application-name> from <source-entity>
[to <destination-host-entity>] with dst <destination-host-entity> [dport <1-65535>]
Where:
Rule ID: This will identify the order the rules are checked against.
Application-name: The rule will apply to the traffic generated by this application.
Source-entity: This can be a zone, network or host. The rule will be applied if the source address in the packets will match against this entity.
To Destination-host-entity: This can be a zone, network or host. The rule will be applied if the source address in the packets will match against this entity.
With Destination-host-entity: As the name implies, this must be a host. With port forwarding rules, this is the destination host where traffic will be forwarded to.
Dport ID: In port forwarding rules this tells the firewall what the NEW destination port is going to be.
Step 1: Configure interfaces.
awplus(config)#interface eth1
awplus(config-if)#ip address 81.100.1.1/30
awplus(config-if)#exit
awplus(config)#vlan database
awplus(config-vlan)#vlan 192
awplus(config-vlan)#exit
awplus(config)#interface vlan192
awplus(config-if)#ip address 192.168.1.254/24
Step 2: Configure private zone.
awplus(config-host)#zone private
awplus(config-zone)#network lan
awplus(config-network)#ip subnet 192.168.1.0/24 interface vlan192
awplus(config-network)#host webserver
awplus(config-host)#ip address 192.168.1.10
Step 3: Configure public zone.
awplus(config-host)#zone public
awplus(config-zone)#network wan
awplus(config-network)#ip subnet 0.0.0.0/0 interface eth1
awplus(config-network)#host int
awplus(config-host)#ip address 81.100.1.1
Step 4: Configure application.
awplus(config)#application port_8888
awplus(config-application)#protocol tcp
awplus(config-application)#dport 8888
Step 5: Configure Network Address Translation (NAT) rules.
awplus(config)#nat
awplus(config-nat)#rule 10 masq any from private to public
awplus(config-nat)#rule 20 portfwd port_8888 from public to public.wan.int
with dst private.lan.webserver dport 80
Step 6: Enable NAT to apply the NAT rules.
awplus(config-nat)#enable
Note that there is a configurable maximum of 500 NAT and/or Firewall rules combined. However, the practical limit may reduce as additional features are configured and used on the device, and depending on the system resources available.
Some useful commands
Verify entity configuration.
awplus#show entity
Example output from the console:
awplus#show entity
Zone: private
Network: private.lan
Subnet: 192.168.1.0/24
Host: private.lan.webserver
Address: 192.168.1.10
Zone: public
Network: public.wan
Subnet: 0.0.0.0/0
Host: public.wan.int
Address: 81.100.1.1
Verify NAT configuration.
awplus#show nat rule
First thing to check is if there is a * symbol next to any of the rules then something is wrong in the way it has been defined.
Example output from the console:
awplus#show nat rule
[* = Rule is not valid - see "show nat rule config-check"]
ID Action App From To With Hits
---------------------------------------------------------------
* 30 masq any private public - 0
10 portfw http public - dmz.a.b 0
Check the hits against the rules. An increasing number of hits means that NAT is working.
A “0” in the hits column may mean something is wrong. You may not be having that type of traffic at that specific moment, but it’s worth investigating.
Check configuration validity of NAT rules
NAT rules are applied to applications and entities. A rule is not valid if either the application, source entity or destination entity the rule applies to is not configured properly.
Use this command to check configuration validity of NAT rules.
awplus# show nat rule config-check
An invalid rule will not be active and cannot be hit.
This command also shows the reasons why a rule is not valid.
Removing the Network Address Translation (NAT) rules
Removing a NAT rule by using the no nat rule command for an actively translated flow does not stop translating immediately. This means subsequent packets in the flow are continued to be translated.
To clear firewall connections, use the command:
awplus# clear firewall connections