Introduction
Private VLANs are VLANs with additional rules.These rules limit the communication that is possible between devices operating within the VLAN. This may be necessary for security reasons. AlliedWare Plus private VLANs provide the ability to divide a VLAN’s ports into separate "groups" and to allow communication within any individual group, but not between groups.
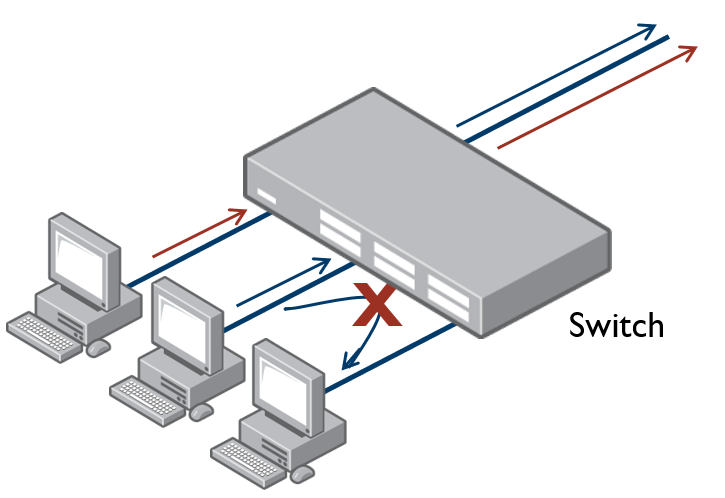
A Private VLAN is a VLAN which contains ports that are prevented from communicating with each other at Layer 2. Also known as port-protected VLANs.
Why I want to configure Private VLANs
On public networks in particular, users can be vulnerable to attack from other users on the same LAN. In addition, there is typically no real need for these users to be able to communicate directly to one another. A private VLAN is a sensible solution. It creates a situation where users are isolated from each other, and are only able to exchange packets with ports that connect to the upstream network.
Some typical scenarios that would benefit from private VLANs include:
- Hotels
- Universities, particularly student accommodation
- Libraries
- Internet cafes
- Hospitals
- Multi Dwelling Unit Internet access via a shared LAN
AlliedWare Plus private VLAN solutions
The primary VLAN is the main VLAN.
The secondary VLANs in the associated set use the primary VLAN to communicate to the rest of the network. In this way, it functions as the "front" VLAN. The primary VLAN contains the promiscuous port, which carries the private VLAN traffic to and from the rest of the network. The promiscuous port is explained in further detail below.
There are two types of secondary VLANs:
Community VLAN - Ports within a community VLAN can communicate with each other, as well as with the promiscuous port. Within a community VLAN, the normal Layer2 switching functionality applies - flooding of broadcast, multicast and unknown unicast packets occurs, just as in a standard VLAN.
Isolated VLAN - The ports in an isolated VLAN are only allowed to communicate via the promiscuous port. Note that ports within different secondary VLANs cannot communicate with each other.
A promiscuous port (also known as the uplink port), is the one port that can communicate with all ports that are members of its associated secondary VLANs. Multiple promiscuous ports can exist in a primary VLAN, but only if the primary VLAN is only associated with community VLANS (that is, that there are no isolated VLANs associated with this primary VLAN).
A promiscuous port is a member of the primary VLAN and all associated secondary VLANs. Its Port VID is set to the VLAN ID of the primary VLAN.
The switch should always use the promiscuous port to connect to the rest of the network.
All the ports in the private VLAN, other than the Promiscuous Port(s), are referred to as host ports. All host ports are members of the Primary VLAN, and of one Secondary VLANs.
Private VLAN configuration
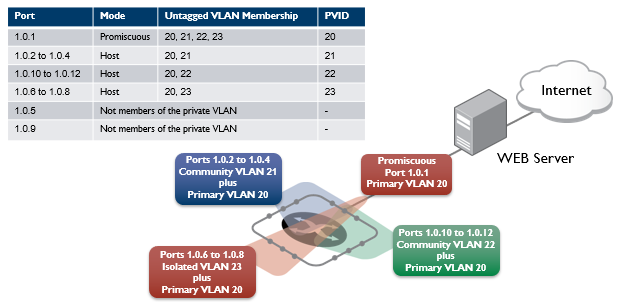
The ports on this Switch have the following configuration:
- Port 1.0.1 is the promiscuous port and is a member of the primary VLAN 20 and all its associated secondary VLANs.
- Ports 1.0.2 to 1.0.4 are members of the community VLAN 21 and are able to communicate with both the promiscuous port and all other ports in VLAN 21.
- Ports 1.0.10 to 1.0.12 are members of the community VLAN 22 and are able to communicate with both the promiscuous port and all other ports in VLAN 22.
- Ports 1.0.6 to 1.0.8 are members of the isolated VLAN 23. Each of these ports can only communicate with the promiscuous port.
Step 1: Create the VLANs
awplus# configure terminal
awplus(config)# vlan database
awplus(config-vlan)# vlan 20-23
Step 2: Set the private VLAN types Set the VLANs to be private and either primary, community, or isolated.
awplus(config-vlan)#private-vlan 20 primary
awplus(config-vlan)#private-vlan 21 community
awplus(config-vlan)#private-vlan 22 community
awplus(config-vlan)#private-vlan 23 isolated
Step 3: Associate the secondary VLANs with the primary VLAN
awplus(config-vlan)#private-vlan 20 association add 21
awplus(config-vlan)#private-vlan 20 association add 22
awplus(config-vlan)#private-vlan 20 association add 23
Step 4: Set port 1.0.1 to be the promiscuous port
awplus(config)#interface port1.0.1
awplus(config-if)#switchport mode private-vlan promiscuous
Step 5: Set the other ports to be host ports
awplus(config)#interface port1.0.2-1.0.4,port1.0.6-1.0.8,port1.0.10-1.0.12
awplus(config-if)#switchport mode private-vlan host
Step 6: On the promiscuous port, map the primary VLAN to each secondary VLAN
awplus(config)# interface port1.0.1
awplus(config-if)# switchport private-vlan mapping 20 add 21-23
Step 7: Associate the community host ports with the community VLANs
awplus(config)#interface port1.0.2-1.0.4
awplus(config-if)#switchport private-vlan host-association 20 add 21
awplus(config)#interface port1.0.10-1.0.12
awplus(config-if)#switchport private-vlan host-association 20 add 22
Step 8: Associate the isolated host ports with the isolated VLAN 23
awplus(config)#interface port1.0.6-1.0.8
awplus(config-if)#switchport private-vlan host-association 20 add 23
To display the private VLAN configuration and associations use this command:
awplus#show vlan private-vlan
PRIMARY SECONDARY TYPE INTERFACES
-------- ---------- --------- -----------
20 21 community port1.0.1 port1.0.2 port1.0.3 port1.0.4
20 22 community port1.0.1 port1.0.10 port1.0.11 port1.0.12
20 23 isolated port1.0.1 port1.0.6 port1.0.7 port1.0.8
Private VLAN suggestions
We recommend to place all host ports into spanning-tree portfast mode and enable BPDU guard.
awplus# configure terminal
awplus(config)# interface port1.0.2
awplus(config-if)# spanning-tree portfast
awplus(config-if)# spanning-tree portfast bpdu-guard enable
Portfast assumes that because host ports will also be edge ports, they will have no alternative paths (loops) via other bridges.
Applying BPDU guard is an extra precaution. This feature disables an edge port if it receives a BPDU frame, because receiving such a frame would indicate that the port has a connection to another network bridge.